Executive summary
- Artificial intelligence in IT security as a tool against new types of threat scenarios.
- Machine learning (ML)/ artificial intelligence (AI) within IT security as a new tool to further advance automation within cyber security.
- Intelligent security services such as Amazon Macie and AWS GuardDuty are examples of a new generation of security.
- A brief look at the supplier market in the cyber security AI environment reveals a (still) very fragmented market.
Current advances in AI have the potential to redefine the way information security works. With the customary fixation on prevention and encryption, IT security departments are unable to support a realignment of IT towards data-centric strategies that companies use to increase the return on their data capital.
This is particularly topical following the release of a European version of Amazon Macie. Amazon Macie is pioneering a new category of AI tools that analyse inventory data.
Using AI to combat the severely underestimated threat of new types of attacks
As a result of ever more networking and the growing number of cognitive systems as well as the new business processes resulting from these, the security landscape is undergoing significant change – particularly within companies. Against this background, it is only logical to make use of AI security tools. It is now up to executives to define and implement the right IT security and data protection strategy to protect infrastructures and data from current threat scenarios and new types of cyber attacks
Users want to apply AI
The fact that users understand the potential that AI has can be seen in a joint TüViT and Cloudflight study entitled “Security by Design”. More than half of users want to use AI solutions in the future, another quarter are still evaluating the situation. In this Expert View, we aim to shed light on which products this could involve and which concrete benefits can be expected. 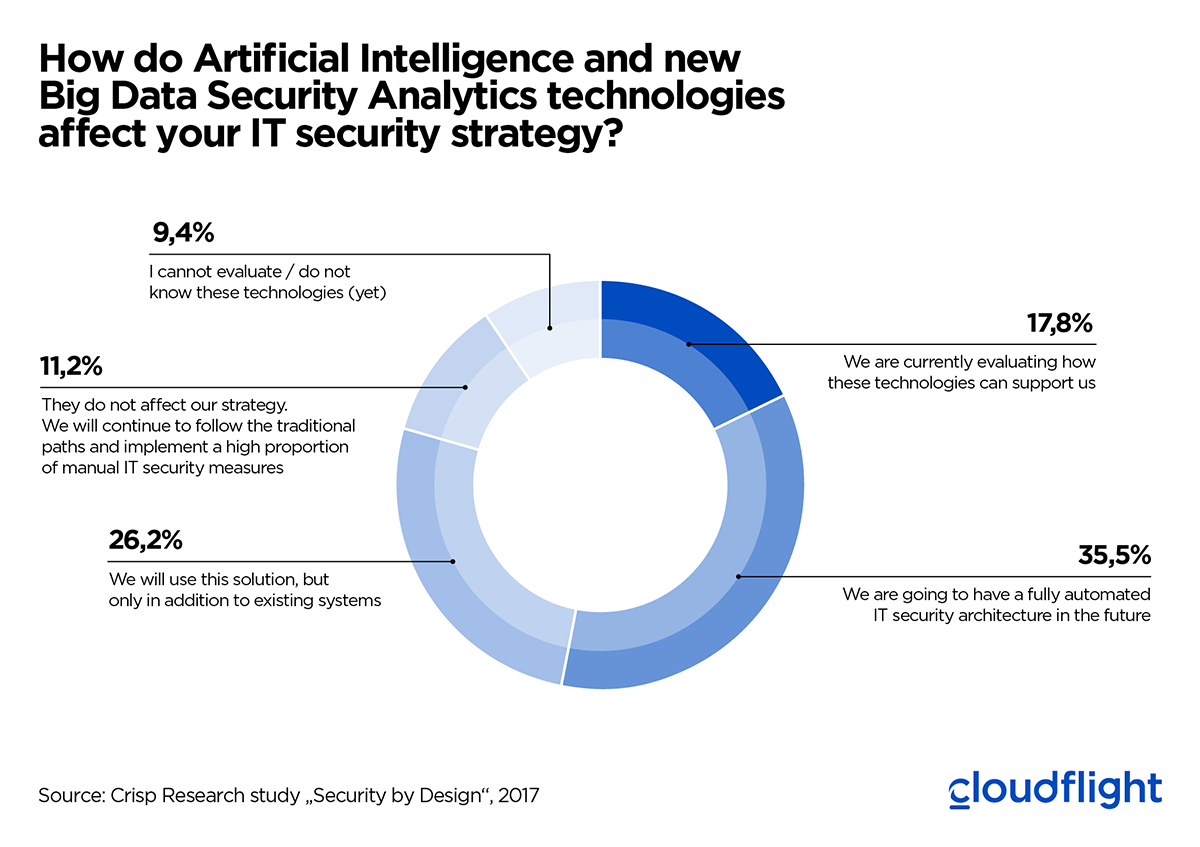
Perspectives provided by machine learning
Implementing security measures in detail has always been incredibly tedious. For example, to find out which data in an unstructured selection contain a reference to persons, each file would have to be inspected individually. When operated by humans, it was, in practical terms, impossible and using general filters did not go far enough.
The GDPR has not made the situation any easier, quite the contrary. With cloud computing, collecting and storing data and logs has become so cheap that we are dealing with ever increasing amounts of data that should be analysed.
Thanks to machine learning security applications, new tools have been created that can be used to further advance automation. The cheaper and better the analysis, the more potential customers will be interested. We believe the coming years will see users talking shop about the advantages and disadvantages of different methods and data sets for training security ML.
A new category of tools
The following features characterise the new category of tools:
- Machine learning – promises to be a real game changer. Analysing data according to patterns with machine learning technology has come a very long way in recent times and promises entirely new and previously unthinkable applications.
- Cloud native – accesses new sensors within the cloud infrastructure and uses the efficiencies of infrastructure on demand to process large amounts of data. Compared to previous agent-based tools, implementation times can be reduced from months to minutes and execution times from batch to interactive.
When taken together, the improvements increase the value of the analysis and allow the user to take immediate action. In the event of an incident, the shorter time needed to react promises to minimise the damage. The low time input could win over other users who have been forced to ignore risks due to a lack of time.
Manufacturers in the security industry already provide a large number of tools, each of which addresses specific target groups. But it was not until the introduction of “Amazon Macie” and “GuardDuty” that machine learning achieved its breakthrough in the security industry. In this respect, AWS has recently introduced two procedures: Macie for inventorying data in S3 buckets and GuardDuty for analysing log files.
Amazon Macie
The characteristics of the new generation are best described with Macie, which AWS has re-released for the European market. Macie can be traced back to the start-up Harvest.ai, which was silently purchased by AWS in 2016. Macie has been in two US availability zones since its launch in Aug 2017 and has now been released in May 2020 as a specially adapted version in the European availability zones (Frankfurt, Dublin, London, Paris).
Simply speaking, Macie is one part security and one part compliance. Macie uses machine learning algorithms to provide unprecedented visibility in security-related or personal data. Macie is used to find anomalies or risky content. Under normal circumstances, you would typically have a warning roughly every 3 days, with the number of false positives being low.
Macie reads files in the Amazon S3 Object Store and classifies their contents based on rules and machine learning. As you can imagine, European customer data looks different to that of US customers, and as a result Macie has been re-trained with European addresses and names, e. g., with UK ID numbers, to be able to locate them reliably in the records. The service is also certified according to ISO 27001, 27018, and with a reference to the Data Processing Addendum (DPA) and the technical-organisational measures (TOM), the formal criteria are also met, which have become more relevant for European customers as a result of the GDPR.
Our analysis has found AWS’s Macie to be a very interesting product for companies of any size and in any industry, also because it is a very cost-effective way to monitor data. As such, Macie has the potential to become a game changer, allowing security departments to evolve from their reactive role to a more active one.
Amazon has also thought about process integration. JIRA integration allows the results to be transformed into tasks or integrated into SIEM platforms such as Splunk or LogRhythm.
AWS GuardDuty
The detection of attempted attacks in logfiles regularly requires evaluations to be fine-tuned to the problem at hand in order to identify attack patterns. As a result, combing through log files is so time-consuming that preventing attacks is usually only possible in theory. In practice, the analysis only takes place after the damage has been done.
Amazon GuardDuty is AWS Macie’s counterpart. While Macie processes the inventory (Data at Rest), GuardDuty guards Data in Transit and analyses log data from the AWS infrastructure (CloudTrail, VPC flow logs, DNS logs), meaning that GuardDuty can automatically deduce threats from this and initiate appropriate countermeasures. While special know-how in network protocols was previously required to evaluate log data, GuardDuty can simply be switched on and gets on with the job. Of course, the messages have to then be processed, most likely by human operators.
GuardDuty is already available in almost all AWS regions, including all European regions. It is also certified, among others according to the German Federal Office for Information Security’s C5 methodology. Guard Duty’s possible applications are down to simplicity and scaling: large companies use GuardDuty as they can turn it on and let it run without much effort, while smaller customers appreciate the simplicity of the first steps in the log analysis.
According to Cloudflight, GuardDuty is aimed more at technical administrators who want to gain insight into data flows, putting them more in the established SIEM category with a smaller but more established interest than already exists for Macie. The advantage of GuardDuty is that it can handle the huge amounts of data that arise without having to export them to other tools.
Market overview: AI in cyber security
In the second part of the Expert View, we add to the overview an analysis of dynamic data that has been established in IT security processes for some time and is available from several manufacturers.
There are a number of providers in the cyber security market and AI can, of course, be found on many a list of features. The market is (still) very fragmented. There is a whole range of providers, which we group as follows:
- First and foremost is IBM Watson, which started using machine learning in many areas early on. IBM’s portfolio is typically tailored to larger companies, and we are not yet seeing the kind of market penetration that one would expect considering their long presence in the market.
- SIEM (Security Information and Event Management) manufacturers that have modernised their portfolio with regard to the cloud or have developed new cloud native products are of interest, among them Cisco, DataDog, LogRhythm, McAfee, RSA, and Splunk. The products are becoming established in the market due to their loyal customer base, which can expect services in line with costs.
- Security manufacturers with typically broad portfolios also offer AI solutions to complement their traditionally signature-based solutions: Avast, Bitdefender, Fortinet, Kaspersky, TrendMicro. The solutions are doing well due to their broad customer base and their well-known range of services. Whether or not the AI components would make a significant difference for the intended use would have to be individually evaluated.
- A whole range of newcomers or start-ups are using the new opportunities in an innovative way with specialised products: Cylance, Ensilo, Exabeam, JASK, iSight (FireEye), Outpost24, Securonix, Trustwave. These can be particularly interesting if the product’s orientation is compatible with one’s own application.
- Among the managed service providers there are as yet few offers with an explicit AI reference. AI seems to have not yet become a differentiating factor there, although machine learning is probably already being used behind the scenes.
In summary, we see that there are already some solutions that allow users to try out the new possibilities of machine learning in cyberspace. Amazon Macie is ideal for AWS customers because of its low entry threshold, where billing is based on usage and integration into the cloud infrastructure. For those who use other cloud providers or their own data centre, we recommend other manufacturers in the SIEM sector, whose interesting offers make it easy to venture into AI.
We would be happy to help you develop and implement a high-level security architecture. We can also, e. g., launch a controlled and systematic attack on a software system with the intention of detecting potential security holes. We have the know-how to locate and plug “any hole” within 24 hours.
